
Joseph Heller, author of Catch 22, famously wrote that “just because you’re paranoid doesn’t mean they aren’t after you.” Many Generation Xers out there may recall that Kurt Cobain also used this quotation in a Nirvana song with a title I can’t repeat in this family-friendly publication. Never mind then (pun intended), the spirit of this quotation, whomever is using it, is that people may always be trying to take something from you whether you care or not.
While your (justified) cybercrime paranoia may lure you into comfort when computing inside the best of (fire)walls, your gut tells you that you are still exposed. How? Perhaps by your email recipients’ nostalgia for their memorable passwords.
When you think about what happens out in the (internet) wild, when you send an email to your lawyer, accountant, realtor, spouse, or friend, do you think they are as cybersecurity conscious or careful as you are? Do you trust all those who your email is forwarded to, to be security conscious enough to protect YOUR information?
You might be living in your e-fortress, but what is somewhat annoying is that you have no visibility into how security aware your email recipients are. And what is terrifying, is knowing that after you click “send”, your sensitive information takes on a life of its own, as it hops around people’s email accounts, often buried in a long-forgotten string of text after many replies and forwards.
Good news. I’d like to announce that we will be running a three-part series (this article included) on cybercriminal Email Eavesdropping™ activities—what it is, how it happens, and how RPost’s RMail tech can actively hunt eavesdroppers and expose them, to pre-empt any damage. (For those who like to read ahead, here is the solution cheat sheet).
Know More:
How to Recall an Email in Outlook
First off, what exactly is Email Eavesdropping™ activity?
We’ll get right down to it. In most cases, it is where a cybercriminal has broken into an email account (think, your recipient, your accountant, etc.) and they patiently eavesdrop on the correspondence until they see that there is some invoice received, wire instructions to fund an account, or escrow transaction details. (For the curious, we’ll explain how, in more detail next week).
At the right time, the eavesdropper performs their trickery (we’ll explain more next week) which ends in attempts to lure people into making a payment to the wrong place (the cybercriminal’s bank account). Amazingly, their success rate today is 5% ($2.4 billion last year) of the total dollar value of attempts (nearly $50 billion last year).
This is so lucrative, that sometimes there are multiple cybercriminals in different countries preying on the same person!
Bottom line: Would you want to be able to see if your email was actively being eavesdropped on at your recipient, in real time? Who wouldn’t!
Stay tuned, as next week we will delve further into the mechanics of these business and email account compromise schemes and begin to acquaint you with RMail’s Email Eavesdropping™ account compromise alerts, and how they can stop these schemes dead in their tracks.
As a teaser, we’ll leave you to ponder this (below) RMail report that identified that a particular recipient’s email account in the Americas was being actively eavesdropped on by cybercriminals in both Asia and Europe nearly simultaneously!
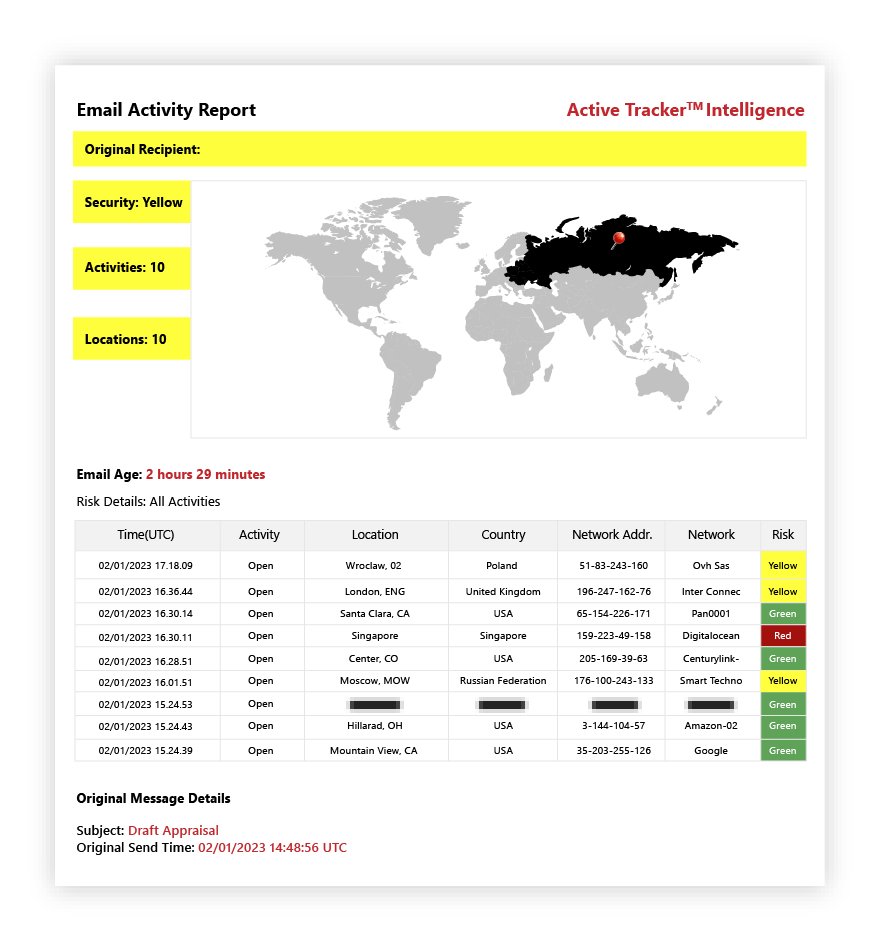
As always, feel free to contact us to discuss RMail, its cutting-edge Email Eavesdropping™ alerts, or if you have any concerns about your own systems being eavesdropped on. We’re always here to help, and there’s nothing wrong with being paranoid in this new era of cybercrime.

February 27, 2026

February 20, 2026
.jpg)
February 13, 2026

February 06, 2026

January 30, 2026