
Armand here, RPost’s product evangelist armadillo, still vacationing on Cape Cod. But as a product enthusiast, I couldn’t help chatting up folks at the 4th of July BBQ about cybersecurity.
Speaking to a multi-family-office real estate investor at the BBQ, he mentioned that one of his colleagues mis-sent $125 million in a San Francisco commercial real estate transaction closing, with the funds ultimately routing off to Nigeria. Yes, $125 million!
How did this happen? He explained that in the days leading up to the closing, there is a flurry of emails from lawyers, various other parties, title insurance closers, and sometimes these are coming in every minute with various comments, document edits, and more about the deal closing. Everyone is moving fast, as a closing like this pays out nice commissions, and time can kill deals. In haste, people are clicking, opening email, editing docs, replying, replying-all… with money on their minds.
In the midst of this, a cybercriminal was eavesdropping on one of the lawyers’ email accounts, and could see the details of the transaction; and could even see the actual documents.
In the midst of the email flurry, the cybercriminal purchased a lookalike domain (domain with one letter off from one of the other parties involved) and cleverly tucked this in the hidden “reply-to” field of the email structure. The cybercriminal then sent the email looking like it was FROM the actual party but with the REPLY-TO going to the cybercriminal’s lookalike domain address. The cybercriminal then, on this particular email, appended a version of the agreement draft that was authentic OTHER THAN the bank account number for the closing funds to be wired. The bank was the same, bank location, bank routing number… all the same. The account number was different. This document then became the “next version” that was circulated by all the parties for the next week up to the closing. At closing, the cybercriminal’s bank account was now baked into the closing documents, and the $125 million was sent… to the closing (cybercriminal) bank account in the USA, and then swiftly routed to another bank, then another, then ended in the cybercriminal’s hands.
Know More: Man in the Middle Attack
There were two main tactics used in this, both of which could have been seen if ANY of the parties had been using the RPost PRE-Crime™ technology.
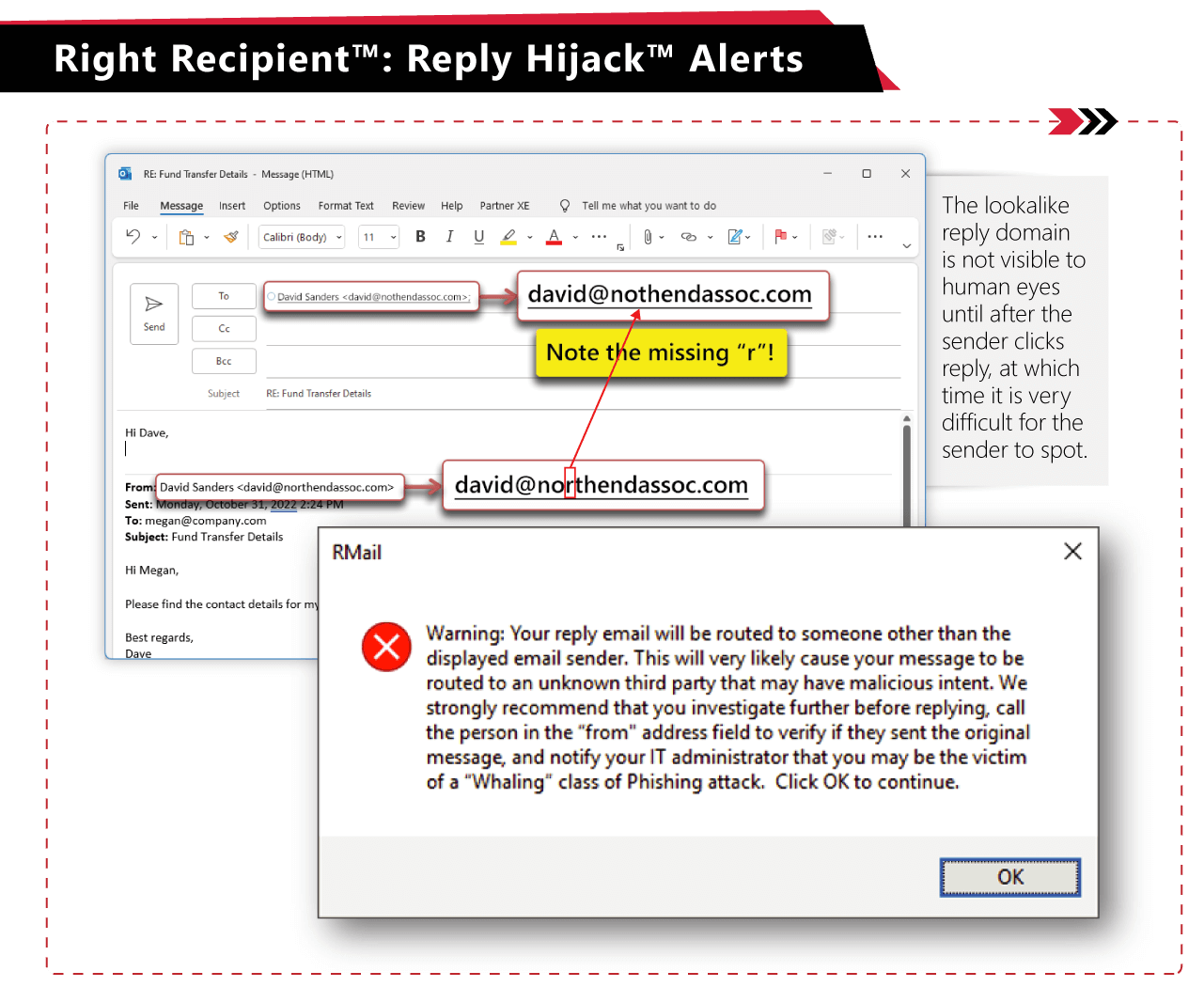
There is a lot to unpack here in this scheme, and there are many interactions that play out. RPost is available to explain more.

February 27, 2026

February 20, 2026
.jpg)
February 13, 2026

February 06, 2026

January 30, 2026