After reading the recent FBI report on the state of email related cybercrime in 2022, one statistic popped out at me, when correlating different parts of the report related to Business Email Compromise and Ransomware.
First, a short refresher.
Business Email Compromise is generally a cybercrime (multi-part attack) that preys on human psychology, with email impostor lures that aim to trick people into mis-wiring invoice payments, home purchase closing funds, investment fundings, and other payments, directing the funds to go to cybercriminal bank accounts in the United States, which then swiftly re-route to cybercriminal international accounts. The FBI says that most people discover and report the mistake 11 days after they mis-sent the funds, yet the only hope according to the FBI of potential recovery is if the mis-wire is reported within 48 hours.
Ransomware, on the other hand, is a crime (direct-attack) injecting file encryption malware into an organization that encrypts critical files on a computer in a way that they can be decrypted if a ransom is paid to the cybercriminal for access to the master file decryption key.
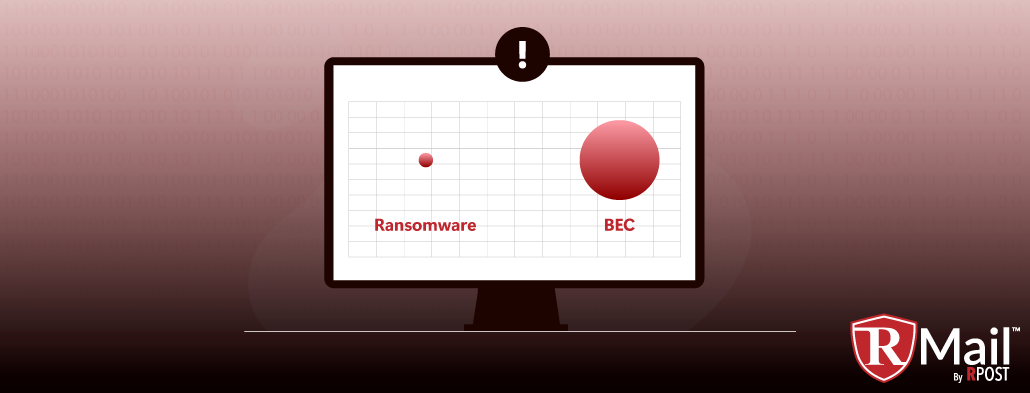
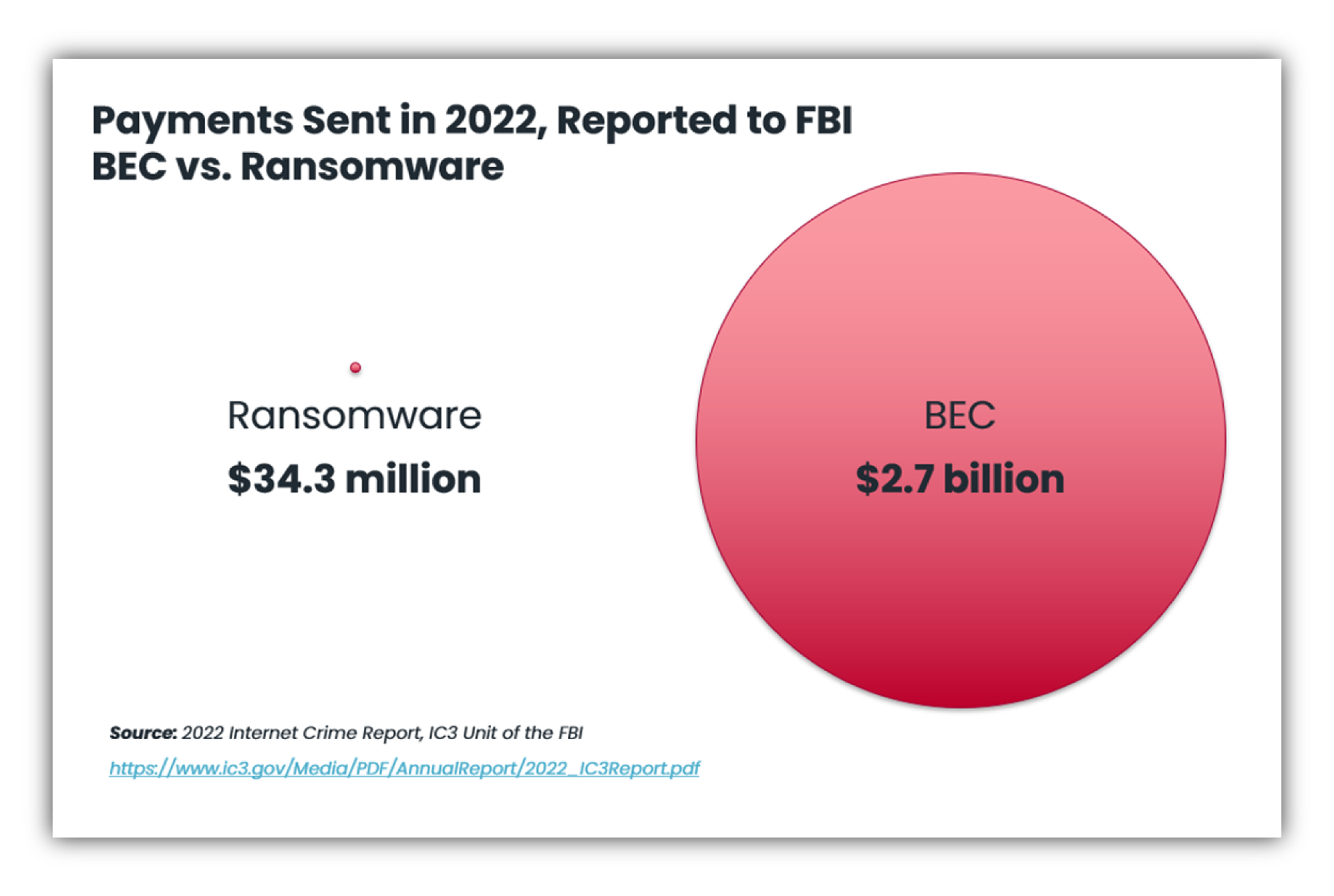
The FBI reports that in the last year, from Business Email Compromise, $2.7 billion was mis-wired to cybercriminal accounts mostly in small amounts of $10K to $250K; most of it unretrievable. According to the FBI, this form of cybercrime is more lucrative than all others for these organized cybercriminal gangs. By contrast, the FBI reports $35 million was paid in ransomware payments, a mere 1% of the losses due to BEC attacks.
Looking at this graphically, you have a huge dot depicting BEC losses, and a tiny dot depicting ransomware losses. Why? Ransomware certainly is prevalent, fierce, and disruptive. How could the losses (ransom payments) be so little in comparison?
Our hypothesis is that inbound anti-virus, malware and other security tools (like Microsoft Defender and others) are (must be) doing a great job in preventing much of the Ransomware attacks, yet Business Email Compromise is much trickier to prevent technically as it preys on human behavior and feelings.
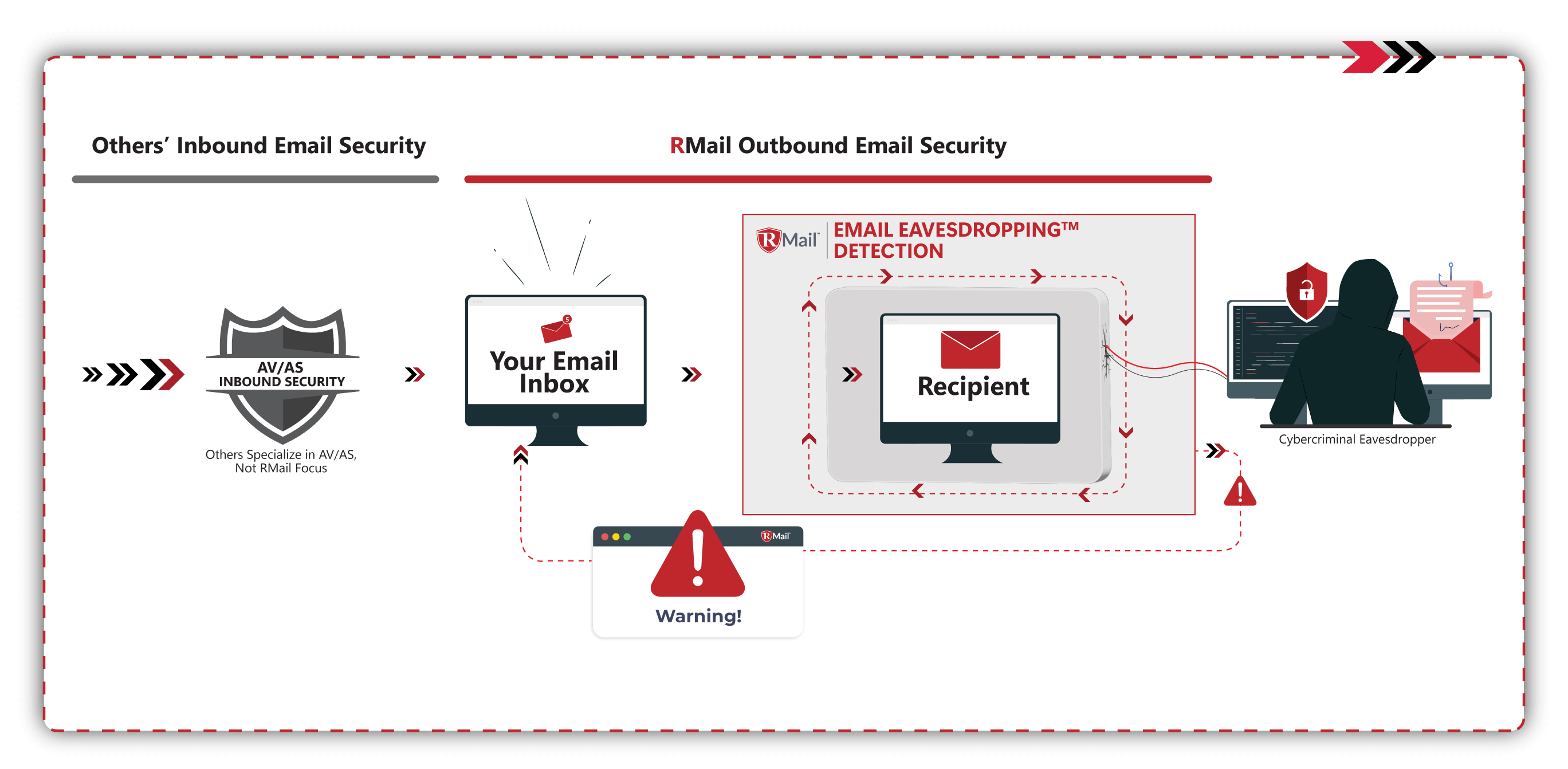
Fortunately, now there is RMail’s PRE-Crime™ module that is designed to prevent, detect and disarm these BEC-initiated wire fraud (mis-payment) attacks by monitoring what is happening outside of one’s email system, after the email is sent and even after delivery to the recipient -- at one’s client for example. It extends peace of mind beyond one’s organization to the entire network of email recipients including their reply and forward recipients. It is designed to pre-empt the cybercrime before the steal; even after the hook is in.
“With RPost's advanced eavesdropping technology, Shaddock National Holdings now has a crucial new tool in our arsenal to detect and thwart wire fraud attempts before they can cause any harm. We are thrilled to have found such a forward-thinking and innovative partner in RPost, who has transformed our email encryption strategy and provided us with a game-changing solution to protect our business and customers,” states Jeff Richardson, Chief Information Officer at Shaddock National Holdings, one of the largest private title insurance companies in the United States.
Deployment only requires changing the outbound mail flow “smart-host” connector to point to the RMail Cloud Gateway or installing the RMail app at the sender; and fine tune Email Eavesdropping settings and other email policies. RMail Email Eavesdropping technology is patented and patent pending. More information is available on the RMail website or contact RPost here.

February 27, 2026

February 20, 2026
.jpg)
February 13, 2026

February 06, 2026

January 30, 2026